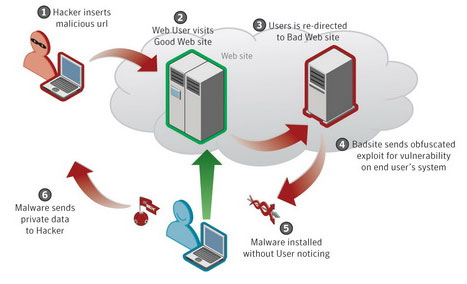
IPA Information-technology Promotion Agency, Japan : IPA/ISEC in JAPAN:virus and UCA incident report for November2010

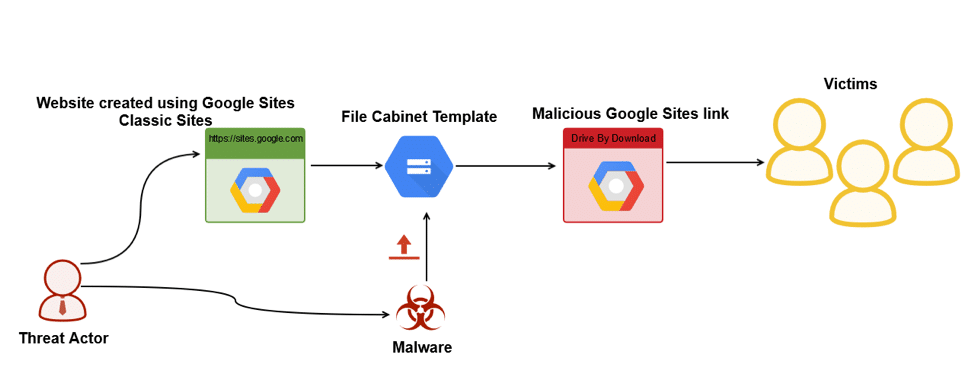
TurkHackTeam EN on Twitter: "Drive-By Download Attack! #cybersecurity #email #attack #drive #cyberpunk #cyber #malware #user https://t.co/w2KRfjAb5j" / Twitter

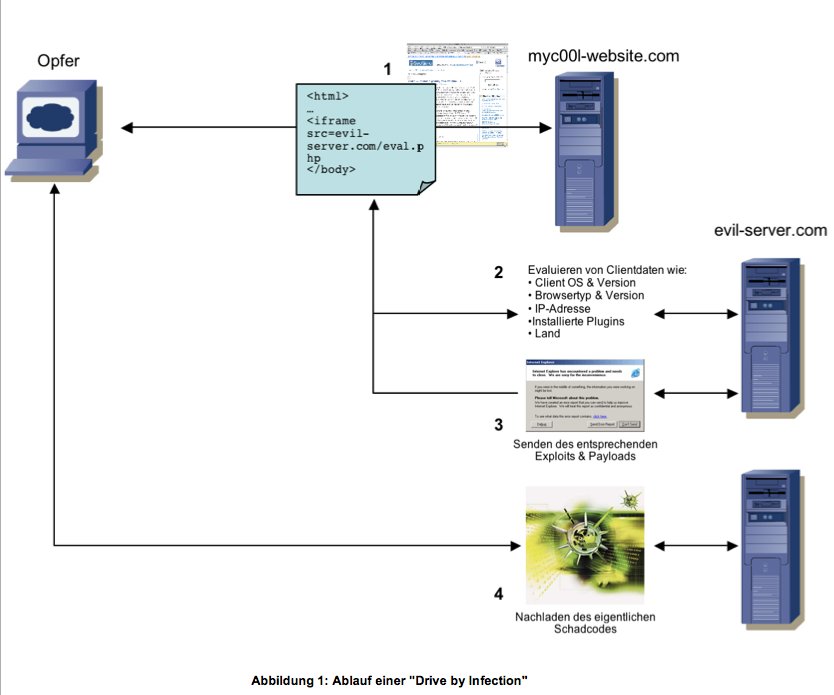
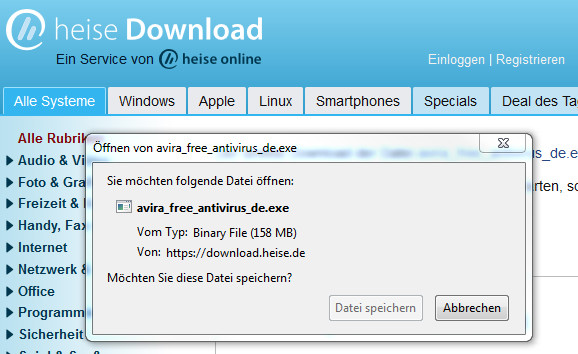
Drive-by-Downloads oder wie man sich bei einem Website-Besuch Malware einfängt - Emsisoft | Sicherheitsblog

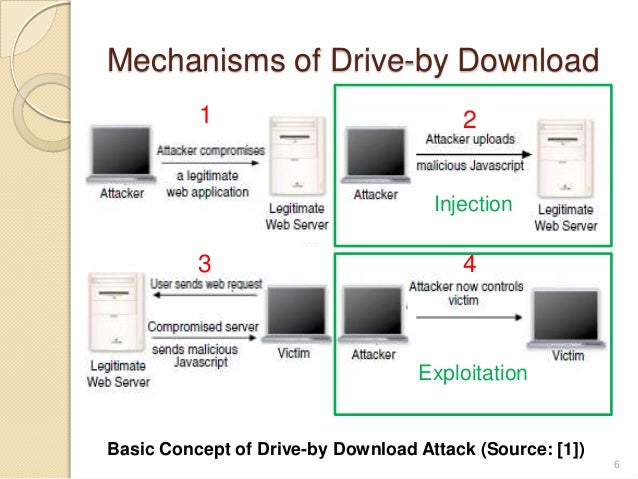
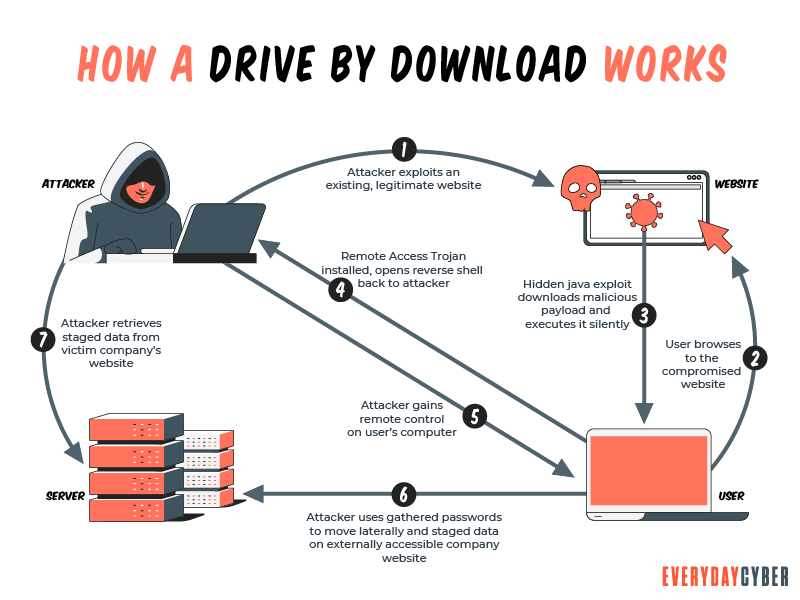
Drive by Download attack scenario Exploit code resides on Attacker Server | Download Scientific Diagram
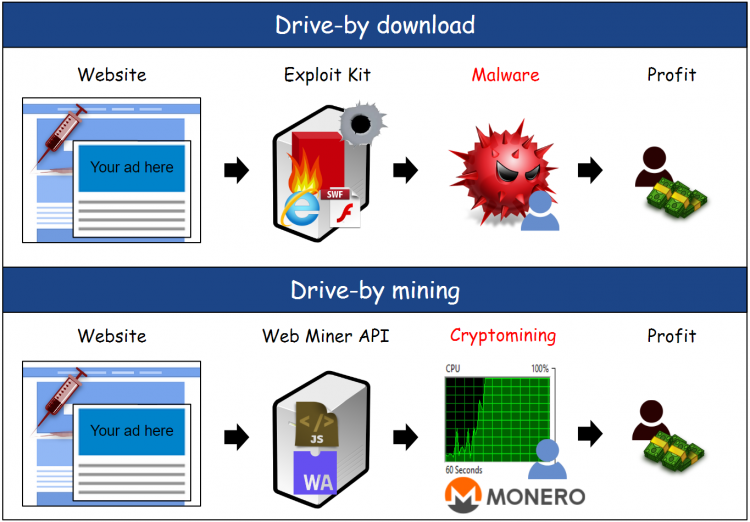
:quality(80)/images.vogel.de/vogelonline/bdb/361100/361163/original.jpg)